Using Microsoft Security Baseline Analyzer
Download MSBA 2.3. Install it and start a default scan on your Windows machine:
Typical results:
- Analyze the report and the proposed solutions.
- Enable the IIS Windows feature.
- Repeat the MSBA scan
- Analyze the new report an compare it with the previous one.
Conclusion?
- As you install applications, you enable services and open communication ports and that creates new vulnerabilities.
- For a home user, the MSBA is a nice little tool to get a glimpse of the security status of your system. But it’s not enough to harden a system for real.
Using the STIG Viewer
In order to harden a standalone Windows machine, the first thing to do is to choose the method or criteria to apply, and the DISA STIGs are the perfect choice for that.
The Windows STIGs are published as a tool to improve the security of DoD information systems. The requirements were developed from Federal and DoD consensus, as well as the Windows Security Guide and security templates published by Microsoft. The vulnerabilities discussed in the Windows 7 STIG are applicable to the Professional, Enterprise and Ultimate Editions.
NOTE: Make sure to test these settings before implementation because they might lead to a loss of required functionality. Furthermore, there are no warranties that the application of all specified configurations will make a system 100 percent secure.
You’ll find a guide to the STIG Viewer tool here.
Using this tool, you can check your system for compliance with hundreds of individual security settings considered important by DISA.
Updating the Windows Security Options File
The requirements in the Window 7 STIG depend on the use of a Microsoft security options file (sceregvl.inf) that has been updated to include additional security checks (“MSS” settings) that are not visible in policies by default. These MSS setting go back to the days before the advent of Trustworthy Computing, when some Microsoft security experts identified about 20 Windows registry values that could be tweaked for what was then perceived to be significant security gain. These entries needed to be loaded into to the local security settings editor and got descriptive names prefixed with “MSS”. An updated copy of the security options file is included with the Windows 7 STIG.
To load the updated Security Options file, complete the following steps:
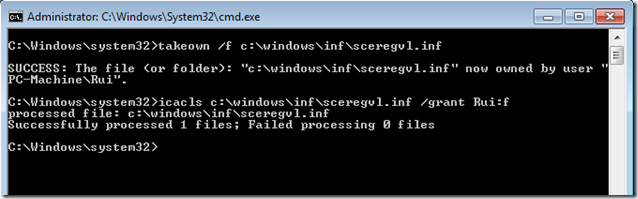
- Open a command prompt with elevated privileges.
- Take ownership of the file with the command
- takeown /f c:\windows\inf\sceregvl.inf
- Add Full permissions with the command
- icacls c:\windows\inf\sceregvl.inf /grant username:f where 'username' is an administrator account.
- Rename the sceregvl.inf file in the %WinDir%\inf directory.
- Copy the sceregvl.inf file provided with the STIG to the %WinDir%\inf directory. The file can be found in the Templates directory included in the STIG zip file.
- Re-register scecli.dll by executing 'regsvr32 scecli.dll' in the command prompt with elevated privileges.
The additional options will now appear in Windows policy tools, such as the Local Security Policy Editor.
NOTE: Another approach to display the same settings will soon be explained in a post about Windows 10
Now all the STIG settings can be applied manually by using the STIG Viewer tool and checking them one by one. You can also create a checklist to keep track of your work as you proceed.
Once you are happy with your settings, you can export them to a new Policy Template that you can later on apply to other machines without having to go through every setting again. If you are using any of the MSS settings, don’t forget to install the updated sceregvl.inf file on every machine.
Using the Security Configuration and Analysis
The SCA tool compares the effective systems settings to a security template that is configured with STIG requirements. The security templates are provided with the STIG zip file in a Templates directory. They are intended for analysis only and can have unknown impacts if used to configure a system without adequate testing.
To load the Security Configuration and Analysis snap-in and analyze the system, perform the following steps:
- Open a command prompt.
- Type "mmc" and Enter.
- Select "File" from the MMC menu bar.
- Select "Add/Remove snap-in" from the drop-down menu.
- Select the "Security Configuration and Analysis" snap-in and click the "Add" button.
- Select "OK".
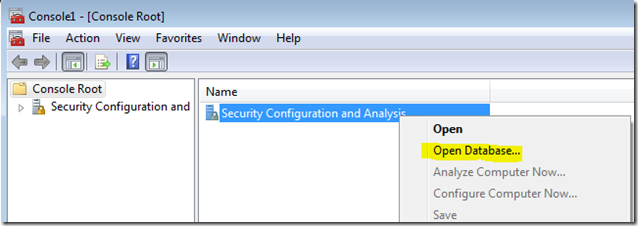
- Right-click on the Security Configuration and Analysis object in the left window.
- Select "Open Database" (this will create the database file if one does not exist).
- Enter a name and path for the database file (e.g., "C:\Test\STIG.sdb"). The path entered must exist prior to this step.
- Select "Open".
- If this was a new database file, a new window will open looking for a template to import. If an existing database file was used, right-click on "Security Configuration and Analysis" in the left pane and select "Import Policy".
- In the "Import Template" window select the appropriate file, in this case U_WinVersion_Analyze_Only.inf which can be found in the Templates directory included in the STIG zip file.
- Check the box to "Clear the database before importing".
- Select "Open".
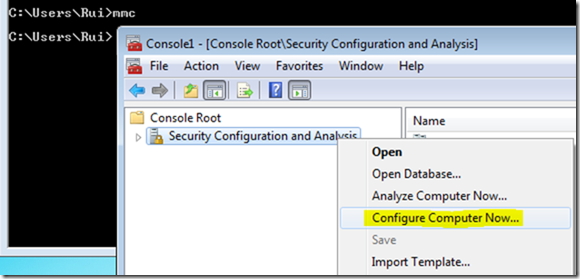
- Right-click on the Security Configuration and Analysis object in the left window.
- Select "Analyze Computer Now…"
NOTE: Do not select "Configure Computer Now…"; this will import the settings in the "Analyze Only" template to the system’s local policy and cannot be undone automatically).
- Enter a name and path for the log file (e.g., "C:\Test\STIG.log").
- Select "OK".
- The Analyzing System Security windows will appear.
- When the analysis is complete, the Security Configuration and Analysis node can be expanded to view current configurations.
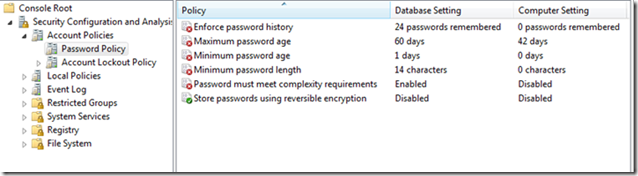
- "Database Settings" are the required settings imported from the analysis template file.
- "Computer Settings" are the effective settings on the system.
- Settings with a green check indicate the Database and Computer settings match.
- Settings with a red x indicate the Database and Computer settings do not match.
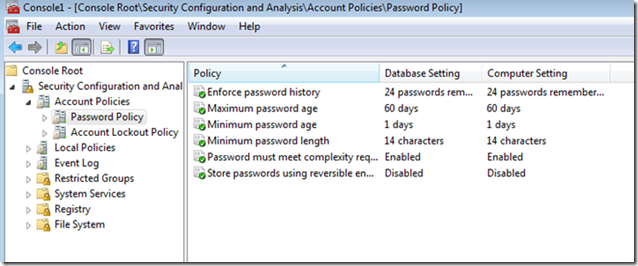
If you are sure you want to apply all the settings:
And now everything will be green for the next analysis:
If you chose to apply only a few settings, in the end you can export the new template and have it installed in other machines by import it.
Previous post: System Hardening
Next post: Windows 7 Hardening (Part II)












2 comments:
Good Bolg. Oracle Fusion SCM Online Training
VERY NICE BLOG Data Entry Work from Home
Post a Comment